DDoS Security

DDoS attacks have risen by 55% and the severity and impacting organizations increased by over 200%. It is alarming, and Organizations must continuously develop a robust DDoS response strategy and be proactive in protecting their public workloads.
DDoS Attacks Classifications, Impact & Protection
DDoS attacks can be simple, but they can be extremely powerful, posing a threat to the existing Internet community. With the rapid advancement of digital transformation and IoT device adoption, the deployment of decentralized technology, and AI technology in the industrial and consumer industries, DDoS attacks have diversified and developed to become increasingly more complex. DDoS attacks can launch in a variety of ways and with a variety of codes and tools.
DDoS attacks have risen by 55% and the severity and impacting organizations increased by over 200%. It is alarming, and Organizations must continuously develop a robust DDoS response strategy and be proactive in protecting their public workloads.

Attacks Classification
Client/Server Botnet
The client-server networking model is widely used and the most common when it comes to network computing. This involves setting up a Command and Control (C&C) server, which transmits and communicates to infected botnets through communications protocol such as Internet Relay Chat (IRC).
P2P Botnet
P2P botnet utilizes the decentralized network technology. In a decentralized network, devices are distributed in a way each device is independent. Unlike Client-server botnet where the client makes request to the server, in P2P botnet each node in the network can function both as a client and a server the reason they have been dubbed Servent (Server + Client)
The Rise Of DDoS Attacks

Attacks Classification
Volumetric (Flood) Attacks
These are the most common types of DDoS attacks that many organizations face. As the name implies, Flooding or Volumes involve bombarding an application, a network, or a server with many requests simultaneously. When the attacker sends these multiple requests simultaneously, the traffic overloads the network’s bandwidth, causing it to fail.
Protocol Attacks
As the name implies, these attacks are directed at internet Protocols. Protocol DDoS attacks target weaknesses in internet communication protocols to cause denial of service (DoS) attacks. These attacks target Layer 3 and Layer 4 protocols, consuming the processing capacity of the infrastructure such as load balancers, servers, and firewalls.
Application Layer Attacks
Application attacks are the most difficult DDoS attacks to detect and, in some situations, mitigate. This attacks target web apps and servers, a site’s content management system (CMS). The attack aims to render the resource unable to produce services, typically achieved by overloading either the RAM or CPU using an HTTP request. This finally ends up within the system getting down to process a high volume of internal requests
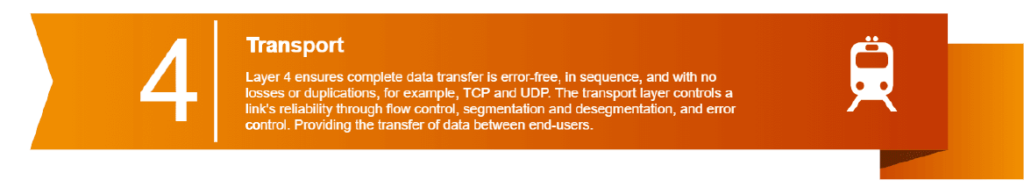
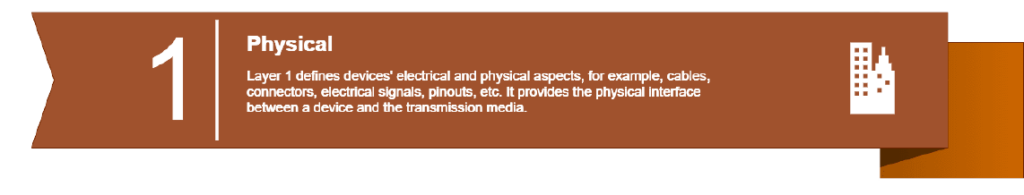
OSI Layer Model Attacks
OSI is the initials for Open Systems Interconnection, which is a conceptual model that harmonizes communications standard protocols between diverse communication systems. In other words, the OSI reference model serves as a common communication standard.
OSI model is a 7-layer architecture. The layers are arranged in a hierarchical way, each layer of the OSI reference model communicates with the layers above and below it and performs specific responsibilities.