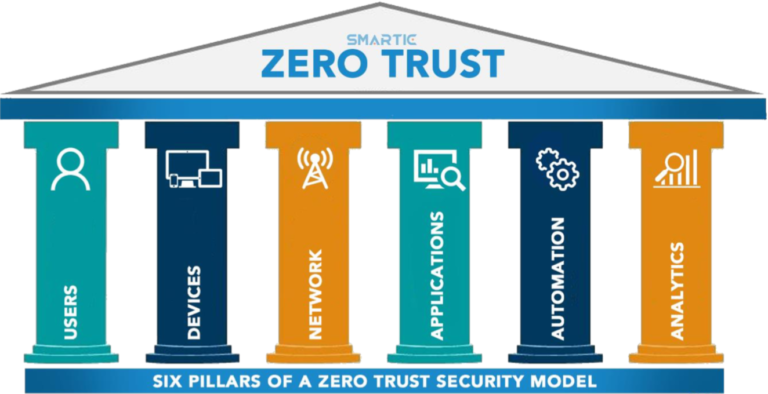
Why Zero-Trust ?
Zero-trust concept dates back to 2008-2009 when some organisations implemented its early vision of zero-trust out of necessity and as prevention measures to secure highly sensitive data. From 2015 zero-trust received its market attention and traction within different government standardization agencies before moving into main stream security technologies.
Nowadays there is a lot of hype around zero-trust, however small percentage of companies have implemented this concept properly and efficiently. Simple concept of “trust no-one” and “verify every transaction” has more to it under the hood. With the mainstream adoption of remote work, usage of cloud infrastructure and increasing number of cybersecurity incidents zero-trust concept starts to find its way in large and medium enterprises.

For Remote Employees
Multiple satellite offices connect to one central headquarters, and there may be several remote employees within an organization. Companies utilize cloud-based resources and applications to connect their teams. The security tools and processes used in the traditional network are ineffective for handling these resources, as they are typically outside the network.
Zero Trust does not require users to connect to the corporate network before accessing cloud resources. For access to be secure and appropriate, it is important to understand the identity of the user and device.
Multi-Cloud and Multi-DCs Networks
Many companies use a combination of datacenters as well as cloud services to run their business. Dynamic provisioning of access to different resources in the company infrastructure, network elements, applications, various development environments and other critical services simplifies user experience as well decreases the possible attack surface for bad actors.
Different cloud providers implement functionality differently, which presents a challenge. Devices that access cloud resources or DCs could also be affected by this, including IoT devices security identity management.
Third-parties, Vendors, Contractors etc.
Multiple satellite offices connect to one central headquarters, and there may be several remote employees within an organization. Companies utilize cloud-based resources and applications to connect their teams. The security tools and processes used in the traditional network are ineffective for handling these resources, as they are typically outside the network.
Zero Trust does not require users to connect to the corporate network before accessing cloud resources. For access to be secure and appropriate, it is important to understand the identity of the user and device.